How to Validate Digital Signatures in a PDF with DocTimeStamp and Long-Term Validation (LTV)
By Laura Massingham | 2023 Aug 22
5 min
Tags
digital signature
webviewer
The use of digital signatures has grown steadily since 2020, with almost 70% of end users now preferring it over handwritten signatures. Digitally signed PDFs are widely used across healthcare, government, and other industries. However, digital signatures on PDF documents do not always guarantee authenticity and validity.
There are a few reasons why PDF signature validation may be required:
- A digitally signed PDF could be altered after signing since PDF contents can be edited with the right tools.
- Advanced signature forgeries can spoof valid signatures by exploiting vulnerabilities in signing formats. The signature appears genuine but is fraudulent.
- User errors such as failing to fully verify a document before signing can allow unintended changes after the fact.
- Signatures may not be properly validated before acceptance, undermining their legitimacy.
In our Ultimate Guide to Digital Signatures, we covered each area of the digital signature technology stack and how the Apryse Developer Suite can meet your signature needs. In this blog we will break down the different methods of digital signature validation and how to apply them with the Apryse SDK.
Learn how digital signatures ensure document authenticity in the age of AI.
Electronic Signature vs Digital Signature
First it is important to define the different types of signatures. Electronic signatures are a simple replacement for a hand-written signature while digital signatures use cryptography to provide document security and authenticity. An e-signature indicates the signer’s intent to sign but doesn’t provide proof of the signer’s identity. For official, sensitive documents that require strong integrity and non-repudiation, verified digital signatures are the way to go.
The advantages of digital signatures include:
- Authentication: A digital signature allows for the precise identification of the signer. When a signature is valid, you can safely assume that you know who signed the document.
- Integrity: A digital signature allows users to easily validate whether the contents of a document have been changed since it was signed.
- Non-repudiation: A digital signature ensures that the signer cannot deny that they signed the document.
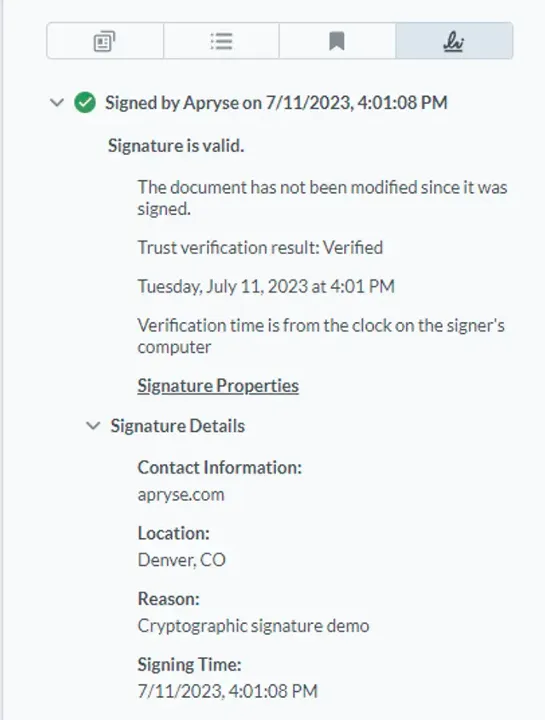
The Apryse SDK enables Signature approvals in PDF documents using a Digital Certificate in accordance with the latest PDF specification. By leveraging public key infrastructure (PKI) technology, with a certificate issued by a trusted certificate authority (CA), a signer can use a certificate-based digital ID to guarantee the authenticity of a signature. Placement of a digital signature using a certificate can also guarantee that a document was not modified since the signature was placed, ensuring the authenticity of the document.
DocTimeStamp
A timestamp prevents digital signature backdating fraud and gives stronger proof of validity and authenticity. It acts like a digital notary, certifying when the signature was applied and with what certificate. If your document requires a timestamp verifiable with a third-party entity (i.e. Certificate Authority), then performing timestamping would allow verification of when the document was signed. A Certificate Authority that hosts a timestamp server publicly is known as a Timestamp Authority (TSA).
Timestamping is achieved by sending a hash of the signature data to the TSA's timestamping server. If the request is determined to be valid, the server will combine the hash provided by the client and an authoritative date-time of timestamping, signed by a private key from the Certificate Authority. The Timestamp Token is then recorded into the document alongside the signature.
To add a DocTimeStamp, first make sure you have the Full API enabled in WebViewer. Then add a DocTimeStamp signature in JavaScript:
async function main() {
const doc = await PDFNet.PDFDoc.createFromFilePath(in_docpath);
doc.initSecurityHandler();
const doctimestamp_signature_field = await doc.createDigitalSignatureField();
const tst_config = await PDFNet.TimestampingConfiguration.createFromURL("URL_to_timestamp_authority");
const opts = await PDFNet.VerificationOptions.create(PDFNet.VerificationOptions.SecurityLevel.e_compatibility_and_archiving);
/* It is necessary to add to the VerificationOptions a trusted root certificate corresponding tothe chain used by the timestamp authority to sign the timestamp token, in order for the timestamp response to be verifiable during DocTimeStamp signing. */
await opts.addTrustedCertificateUString(in_trusted_cert_path);
/* By default, we only check online for revocation of certificates using the newer and lighter OCSP protocol as opposed to CRL, due to lower resource usage and greater reliability. However, it may be necessary to enable online CRL revocation checking in order to verify some timestamps
(i.e. those that do not have an OCSP responder URL for all non-trusted certificates). */
await opts.enableOnlineCRLRevocationChecking(true);
const widgetAnnot = await PDFNet.SignatureWidget.createWithDigitalSignatureField(doc, new PDFNet.Rect(0, 100, 200, 150), doctimestamp_signature_field);
await (await doc.getPage(1)).annotPushBack(widgetAnnot);
// (OPTIONAL) Add an appearance to the signature field.
const img = await PDFNet.Image.createFromFile(doc, in_appearance_img_path);
await widgetAnnot.createSignatureAppearance(img);
console.log('Testing timestamping configuration.');
const config_result = await tst_config.testConfiguration(opts);
if (await config_result.getStatus()) {
console.log('Success: timestamping configuration usable. Attempting to timestamp.');
} else {
// Print details of timestamping failure.
console.log(await config_result.getString());
if (await config_result.hasResponseVerificationResult()) {
const tst_result = await config_result.getResponseVerificationResult();
console.log('CMS digest status: ' + await tst_result.getCMSDigestStatusAsString());
console.log('Message digest status: ' + await tst_result.getMessageImprintDigestStatusAsString());
console.log('Trust status: ' + await tst_result.getTrustStatusAsString());
}
return false;
}
await doctimestamp_signature_field.timestampOnNextSave(tst_config, opts);
// Save/signing throws if timestamping fails.
await doc.save(in_outpath, PDFNet.SDFDoc.SaveOptions.e_incremental);
}
PDFNet.runWithCleanup(main); Reference our full guide for more information about trusted certificates and to add a DocTimeStamp signature using JavaScript. Full code samples are available to demonstrate using the digital signature API to digitally sign, certify, and/or verify PDF documents in all supported languages.
Long Term Validation (LTV)
Taking your security measures one step further, Long-Term Validation (LTV) can be used to validate a digital signature anytime in the future, regardless of changes to specifications. It provides an additional layer of validation for long-term digital signature validation in PDFs and other documents. When a document is signed, the status of the signing certificate is captured and embedded within the PDF. This includes validity at signing time. This means that even if the certificate subsequently expires or is revoked, the signature remains verifiable using the LTV data to check the status at signing time rather than the current status.
WebViewer and server-side SDKs allow adding trusted timestamps and embedding certification validation data during signing.WebViewer also allows validating LTV data to confirm signatures are intact. The viewer can check that the document has not changed since the initial signing, providing long-term assurance of authenticity and integrity.
async function main() {
const opts = await PDFNet.VerificationOptions.create(PDFNet.VerificationOptions.SecurityLevel.e_compatibility_and_archiving);
await opts.addTrustedCertificateUString(in_trusted_cert_path);
/* By default, we only check online for revocation of certificates using the newer and lighter OCSP protocol as opposed to CRL, due to lower resource usage and greater reliability. However, it may be necessary to enable online CRL revocation checking in order to verify some timestamps (i.e. those that do not have an OCSP responder URL for all non-trusted certificates). */
await opts.enableOnlineCRLRevocationChecking(true);
const timestamp_verification_result = await doctimestamp_signature_field.verify(opts);
if (!(await doctimestamp_signature_field.enableLTVOfflineVerification(timestamp_verification_result))) {
console.log('Could not enable LTV for DocTimeStamp.');
return false;
}
await doc.save(in_outpath, PDFNet.SDFDoc.SaveOptions.e_incremental);
}
PDFNet.runWithCleanup(main);Long-term validation information for a signature assumes and uses a DocTimeStamp for the addition of LTV. Check out this guide and code samples in every supported language here.
Conclusion
Digital signatures can save both time and money by reducing paper dependence and simplifying workflows in distributed work environments. Additionally, they offer the user-friendly experience that consumers have come to expect from their vendors and applications. Check out the legislation that governs your locations of operation and industry, then head over to our documentation and download the latest SDK to build and test files for your operating system.
You can check out our interactive demo for a demonstration of how digital signatures work in the Apryse WebViewer, or see the documentation for the Web SDK to get started quickly. Don’t forget you can also reach out to us on Discord if you have any issues.
Tags
digital signature
webviewer

Laura Massingham
Director of Product Marketing
Related Products
WebViewer
Share this post



