Ian Morris
Technical Writer
Updated July 09, 2025
4 min
Secure Redaction in Healthcare: A Focus on HIPAA Compliance
Ian Morris
Technical Writer
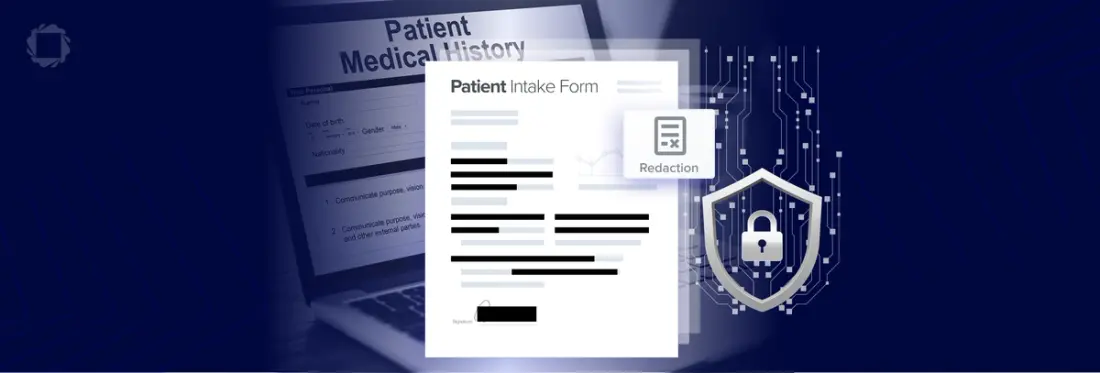
Summary: A redaction SDK is crucial for healthcare apps and software because it ensures the secure and compliant handling of sensitive patient information. It allows for the automatic redaction of personal data in documents, protecting patient privacy and meeting regulatory requirements like HIPAA. This enhances data security and reduces the risk of data breaches.
Introduction
In the healthcare industry, ensuring the security of confidential patient information is not just desirable but a legal obligation. The Health Insurance Portability and Accountability Act (HIPAA) mandates stringent measures to safeguard the confidentiality, integrity, and availability of patient data shared between healthcare providers and business associates. One such measure is the HIPAA Privacy Rule, which requires the removal of sensitive data from health information; a process also known as redaction.
We’ve written previously about how the secure redaction capabilities of the Apryse WebViewer SDK can serve the needs of the legal and financial sectors. In this article, we’ll explore how healthcare companies can leverage WebViewer to meet these compliance requirements.
What is Redaction Anyway?
First, let’s explain what we mean by redaction and secure (or “true”) redaction. In essence, redaction describes various ways of concealing or eliminating confidential information from documents. Secure redaction specifically refers to the physical removal of the chosen content and all related metadata, ensuring it cannot possibly be recovered.
For more background, see our Ultimate Redaction Guide to learn more about redaction techniques and what can go wrong if it’s not done correctly.
Digital Transformation in Healthcare
As with many industries, the healthcare sector is increasingly reliant on electronic data. Digital transformation of document processes has become more and more prevalent, especially since the COVID-19 pandemic required medical services to adapt quickly to the situation.
The rate of digitalization significantly accelerated during the pandemic, with demand for digital access at an unprecedented level. Healthcare was transformed by the immediate need for digital-first strategies, with telemedicine and remote monitoring being rapidly adopted to enable healthcare provision without physical interaction.
In turn, collaboration between healthcare professionals and providers was similarly revolutionized. Health data sharing between electronic health record (EHR) systems was essential in tracking and containing the virus and treating patients, and this trend for EHR interoperability at all points of the healthcare system has continued.
While this shift has brought many benefits, particularly in providing access to telehealth for those in rural areas, it also introduced new compliance challenges in terms of data privacy and security.
Data Privacy and Compliance Requirements
One of these challenges is the need to secure confidential and sensitive information in digital records such as EHRs. Signed into US federal law in 1996, HIPAA aims to protect sensitive health information from being disclosed without the patient’s knowledge or consent. This introduced specific requirements to govern the protection of personal data in healthcare, which are defined by the HIPAA Privacy Rule.
Similar legislation exists in other countries and regions. In Canada there is the Personal Information Protection and Electronic Documents Act (PIPEDA), while the European Union’s General Data Protection Regulation (GDPR) applies to healthcare and life sciences, as well as other industries.
Since HIPAA is healthcare-specific legislation, we’ll concentrate on meeting its compliance requirements. However, data privacy and protection regulations around the world have similar obligations for the healthcare and related sectors. So, wherever you are in the world, this advice should be generally applicable.
What Does HIPAA Compliance Require?
HIPAA mandates stringent measures to safeguard the following:
- Personal Identifiable Information (PII) refers to any data that can be used to identify an individual, either directly or indirectly. This could include names, social security numbers (SSNs), phone numbers, addresses, and email addresses.
- Protected Health Information (PHI), meanwhile, is a specific category of PII. This includes any health-related information that can be associated with a particular individual. HIPAA defines PHI as including medical records, billing details, health insurance specifics, plus any other data collected by a healthcare provider or health insurance plan to provide care or coverage.
Healthcare providers and insurance companies, recognized as “covered entities” under HIPAA, are obligated to follow several rules to uphold patient confidentiality and ensure adherence to the Act:
- Privacy: They are required to honor the rights of patients to their PHI. This includes granting patients access to their health records, providing them with a copy, and allowing them to make corrections.
- Security: They must put in place physical, technical, and administrative security measures to protect health information that is stored or transferred electronically.
- Enforcement: They are required to cooperate with investigations into a breach.
- Breach Notification: In the event of a breach, they must follow certain procedures to inform the individuals affected.
- Business Associate Compliance: If a covered entity employs a business associate to assist with its healthcare activities and functions, the covered entity must have a written contract or other agreement with the business associate. This agreement must clearly define the tasks of the business associate and require the associate to adhere to the Rules’ requirements for the protection of privacy and security of PHI.
- Compliance with the Omnibus Rule: This rule makes business associates of covered entities directly responsible for complying with certain requirements of the HIPAA Rules.
These requirements aim to safeguard the privacy of individuals’ health information while enabling covered entities to embrace new technologies to enhance the quality and efficiency of patient care.
The Dangers of Non-Compliance
Failure to comply with HIPAA can lead to civil and criminal penalties, including fines up to $1.5 million per year for each violation. While over in Europe, GDPR violations can result in fines of up to €20 million or 4% of the company's global annual turnover, whichever is higher.
Such penalties are not just empty threats. A 2021 data leak concerning almost 500,000 persons resulted in a software company receiving a 1.5 million euro fine for failing to secure health data, the maximum amount permitted by French regulations.
Moreover, non-compliance can lead to reputational damage, loss of patient trust, and potential legal action. Therefore, it's crucial for healthcare organizations to implement robust data protection measures, including secure redaction of PII and PHI.
The Need for Secure Redaction in Healthcare
In the healthcare industry, information is commonly shared between healthcare providers, insurance companies, and other parties. For compliance with HIPAA requirements, PII and PHI may need to be securely removed from medical records, insurance claims, and other documents, before being shared with third parties.
For example, a hospital may share a patient's medical records with an insurance company for billing purposes. Since these records likely contain sensitive information such as the patient's name, address, social security number, and medical history, these would first need to be redacted.
However, traditional redaction methods, such as manual redaction or simple black-out tools, are not sufficient in the digital age. These methods can be time-consuming, prone to human error, and may not completely remove the sensitive information. For instance, metadata, bookmarks, or hidden layers in a PDF document may contain information that should also be redacted.
Using WebViewer to Securely Redact PHI and PII
To ensure compliance with the HIPAA requirements, here’s how you could utilize the Apryse WebViewer to de-identify PHI and PII from a document before sharing it with another provider.
WebViewer’s redaction capabilities are powerful yet incredibly easy to use. When viewing a document, simply click the redaction tool icon and click and drag to select specific content to be redacted.
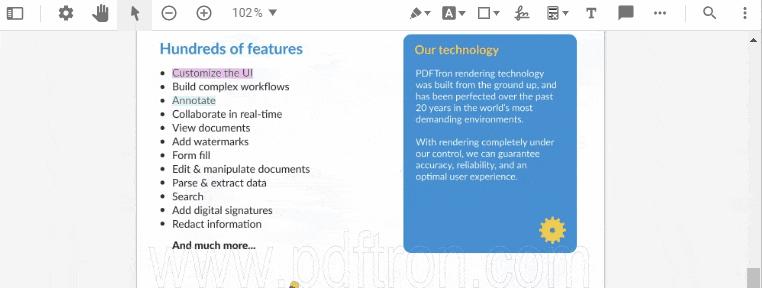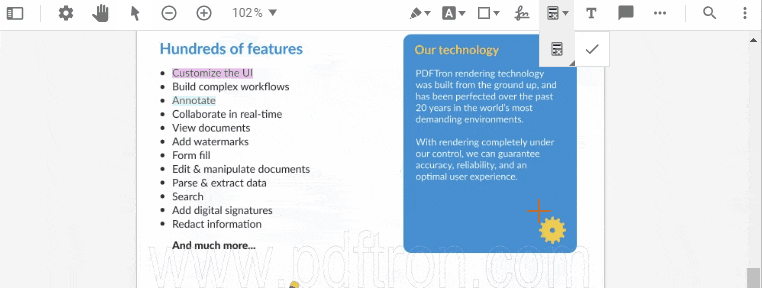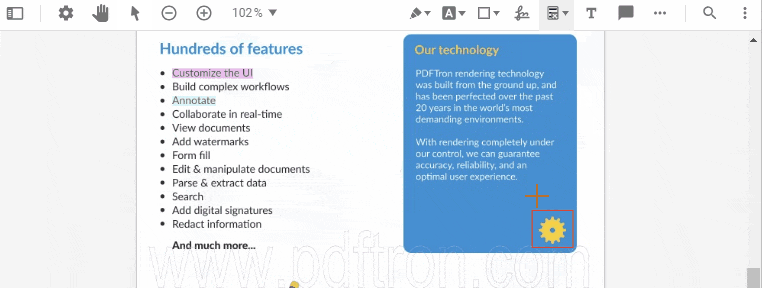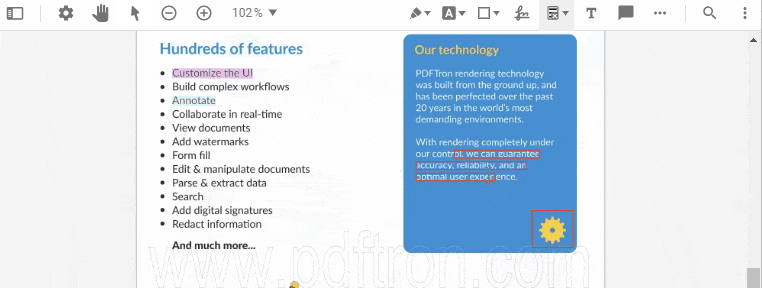
Creating a new redaction annotation.
Content selected for redaction can be reviewed before applying the redaction operation, which physically removes the content from documents, ensuring that the sensitive information cannot be retrieved.
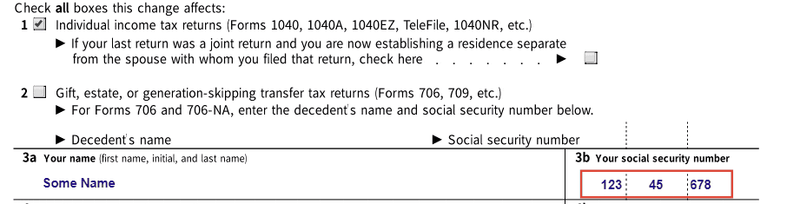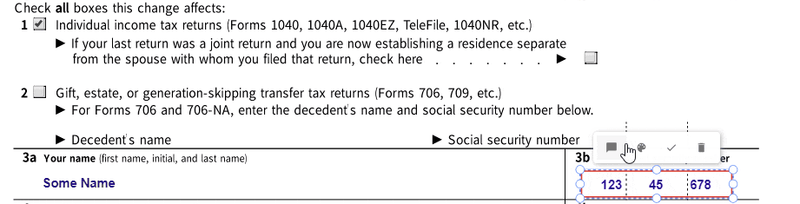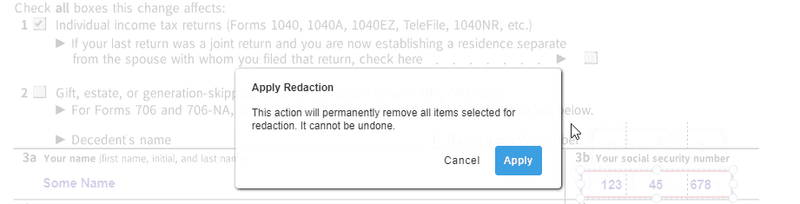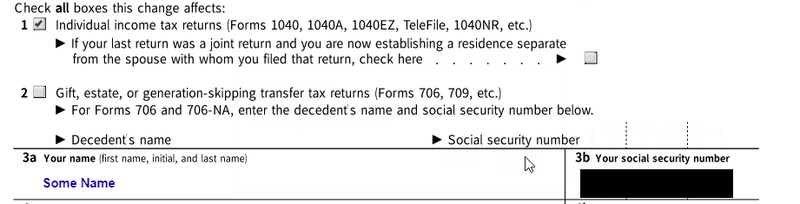
Applying a selected redaction.
You can also redact areas of images and text and even entire pages from documents. This is all covered in the following video on our YouTube channel, which walks you through the process of searching and redacting for PII and PHI:
Stepping Things Up a Notch: Automated Redaction
If you’d like to get a little more advanced, redaction templates can also be created with predefined redaction annotations for documents with consistent, unchanging layouts.
That’s not all though. Since WebViewer is an SDK, of course you can fully automate redaction operations too. See our comprehensive documentation to learn how to create and apply redactions programmatically.
If you’d like to try out WebViewer’s redaction functionality for yourself, the redaction demo on our Showcase site shows just how intuitive the process is.
Custom Integration of Apryse WebViewer
Healthcare organizations can leverage the WebViewer SDK’s advanced capabilities to bring the power of the Apryse SDK to web applications, including its best-in-class redaction capabilities.
WebViewer’s user-friendly and collaborative interface can be easily embedded into web applications that require advanced document-handling capabilities, such as custom healthcare portals and online collaboration platforms.
Documents of almost any file type can be redacted since the WebViewer supports over 30 different document types, including PDFs, Microsoft Office files, and more.
WebViewer SaaS Plugins and Salesforce Integration
WebViewer plugins are available for low-code SaaS platforms and environments like Appian, Mendix, OutSystems, and SharePoint, providing users with a high-quality, customizable and secure document experience - free from server-side dependencies.
Thanks to WebViewer’s support for Salesforce integration as a Lightning Web Component, healthcare providers using the popular Salesforce Health Cloud health platform benefit from not just fully-integrated secure redaction, but also a comprehensive and collaborative document experience. Check out the Salesforce WebViewer documentation to get started.
Conclusion
Secure redaction is a critical part of data privacy and security in the healthcare industry. By understanding the requirements of HIPAA and similar legislation, healthcare organizations can protect sensitive information, ensure regulatory compliance, and maintain the trust of their patients.
The Apryse WebViewer excels at displaying, modifying, and handling PDFs and many other document types. Thanks to its intuitive secure redaction capabilities, it is also the natural choice for healthcare redaction needs, and many other industries.
In addition to its abilities for manual, text-based, and pattern-based redaction, it is even capable of eliminating content that isn’t visible on the page, such as document metadata or bookmarks.
When you’re prepared to begin, consult the SDK documentation to get started quickly. Remember, if you encounter any problems, you can always contact us on Discord.


